Abstract
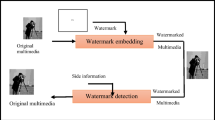
A scheme which integrates image compression and image watermarking in an effective way is proposed in this research. The image compression scheme under consideration is EBCOT (Embedded Block Coding with Optimized Truncation) which has been adopted in the verification model (VM) of the emerging JPEG-2000 image compression standard. The watermark is embedded during the process when the compressed bit-stream is formed, and can be detected on the fly in image decoding. Thus, watermark embedding and retrieval can be done very efficiently in comparison with other existing watermarking schemes. In addition to efficiency, the proposed scheme has many interesting features. The embedded watermark is robust against various signal processing attacks such as coding and filtering while the watermarked image maintains good perceptual quality. The watermark retrieval procedure does not require the knowledge of the original image. Furthermore, the watermark can be detected progressively and region of interest (ROI) watermarking can be accomplished easily.
Similar content being viewed by others
References
M.D. Swanson, M. Kobayashi, and A.H. Tewfik, “Multimedia Data Embedding and Watermarking Technologies, ” Proceeding of IEEE, vol. 86, no. 6, 1998, pp. 1064–1087.
F. Hartung and M. Kutter, “Multimedia Watermarking Tech-niques, ” Proceeding of IEEE, vol. 87, no. 7, 1999, pp. 1079–1107.
R.B. Wolfgang, C.I. Podilchuk, and E.J. Delp, “Perceptual Wa-termarking for Digital Images and Video, ” Proceeding of IEEE, vol. 87, no. 7, 1999, pp. 1108–1126.
G. Caronni, “Assuring Ownership Rights for Digital Images, ” in Proc.VIS 95; Session Reliable IT Systems, Vieweg, Germany, 1995, pp. 251–263.
K. Tanaka, Y. Nakamura, and K. Matsui, “Embedding Secret In-formation into a Dithered Multi-Level Image, ” in Proc.1999 IEEE Military Communications Conference, Monterey, CA, 1990, pp. 216–220.
R.G. van Schyndel, A.Z. Tirkel, and C.F. Osborne, “A Digital Watermark, ” in Proc.1994 IEEE Int.Conf.on Image Process-ing( ICIP), Austin, TX, 1994, vol. 2, pp. 86–90.
W. Bender, D. Gruhl, N. Morimoto, and A. Lu, “Techniques for Data Hiding, ” in IBM Syst.Journal, 1996, vol. 35, no. 3/4, pp. 313–316.
A. Piva, M. Barni, F. Bartolini, and V. Cappellini, “DCT-Based Watermark Recovering Without Resorting to the Uncorrupted Original Image, ” in Proc.1997 IEEE Int.Conf.on Image Pro-cessing( ICIP), Santa Barbara, CA, 1997, vol. 1, pp. 520–523.
I.J. Cox, F.T. Leighton, and T. Shamoon, “Secure Spread Spec-trum Watermarking for Images, Audio and Video, ” in Proc.1996 IEEE Int.Conf.on Image Processing(ICIP), Lausanne, Switzerland, 1996, pp. 243–246.
X.G. Xia, C.G. Boncelet, and G.R. Arce, “A Multisolution Watermark for Digital Images, ” in Proc.1997 IEEE Int.Cont.on Image Processing(ICIP), Santa Barbara, CA, vol. 1, 1997, pp. 548–551.
C.I. Podilchuk and W. Zeng, “Image-Adaptive Watermarking Using Visual Models, ” in IEEE Journal on Selected Areas in Communications, vol. 16, no. 4, 1998, pp. 525–539.
H.-J. Wang, P.-C. Su, and C.-C.J. Kuo, “Wavelet Based Blind Watermark Retrieval Technique, ” in 1998 SPIE Photonics East-Symposium on Voice, Video, and Data Communications, Boston, MA, 1998.
C. Chrysafis, D. Taubman, and A. Drukarev, “Overview of JPEG2000, ” in Proc.1999 PICS 52nd Annual Conference, Savannah, GA, 1999, pp. 333–338.
JPEG 2000 Document, “JPEG 2000 Verification Model 5.0 (Technical description), ” ISO/IEC JTC1/SC29/WG1 N1409, July 1999.
A. Said and W.A. Pearlman, “A New, Fast, and Efficient Image Codec Based on Set Partitioning in Hierarchical Trees, ” in IEEE Trans.on Circuits and Systems for Video Technology, vol. 6, 1996, pp. 243–250.
J. Shapiro, “Embedded Image Coding Using Zerotrees of Wavelet Coefficients, ” in IEEE Trans.on Signal Processing, vol. 4, 1993, pp. 3445–3462.
H. Stark and J.W. Woods, Probability, Random Processes and Estimation Theory for Engineers, Englewood Cliffs, NJ: Pren-tice Hall, 1994.
M.-Y. Shen and C.-C.J. Kuo, “Artifact Reduction in Low Bit Rate Wavelet Coding with Robust Nonlinear Filtering, ” in Proc.1998 IEEE Second Workshop on Multimedia Signal Processing, Redondo Beach, CA, 1998, pp. 480–485.
P.-C. Su, H.-J.M. Wang, and C.-C.J. Kuo, “Digital Image Watermarking in Regions of Interest, ” in Proc.1999 PICS 52nd Annual Conference, Savannah, GA, 1999, pp. 295–300.
Author information
Authors and Affiliations
Rights and permissions
About this article
Cite this article
Su, PC., Wang, HJ.M. & Kuo, CC.J. An Integrated Approach to Image Watermarking and JPEG-2000 Compression. The Journal of VLSI Signal Processing-Systems for Signal, Image, and Video Technology 27, 35–53 (2001). https://doi.org/10.1023/A:1008111228727
Published:
Issue Date:
DOI: https://doi.org/10.1023/A:1008111228727