Abstract
Today’s smartphones are equipped with a large number of powerful value-added sensors and features, such as a low-power Bluetooth sensor, powerful embedded sensors, such as the digital compass, accelerometer, GPS sensors, Wi-Fi capabilities, microphone, humidity sensors, health tracking sensors, and a camera, etc. These value-added sensors have revolutionized the lives of the human being in many ways, such as tracking the health of the patients and the movement of doctors, tracking employees movement in large manufacturing units, monitoring the environment, etc. These embedded sensors could also be used for large-scale personal, group, and community sensing applications especially tracing the spread of certain diseases. Governments and regulators are turning to use these features to trace the people’s thoughts to have symptoms of certain diseases or viruses, e.g., COVID-19. The outbreak of COVID-19 in December 2019, has seen a surge of the mobile applications for tracing, tracking, and isolating the persons showing COVID-19 symptoms to limit the spread of the disease to the larger community. The use of embedded sensors could disclose private information of the users, thus potentially bring a threat to the privacy and security of users. In this article, we analyzed a large set of smartphone applications that have been designed to contain the spread of the COVID-19 virus and bring the people back to normal life. Specifically, we have analyzed what type of permission these smartphone apps require, whether these permissions are necessary for the track and trace, how data from the user devices are transported to the analytic center, and analyzing the security measures these apps have deployed to ensure the privacy and security of users.
Keywords: Contact-tracing applications, COVID-19, pandemic response, privacy preservation, security
I. Introduction
It is believed that a virus that causes the novel COVID-19 disease spreads mainly from having a close interaction or contact with the person already being affected with the virus, and still carrying the attributes of the virus. Since December 2019, the work has already begun on the development of a potential vaccine for the cure, however, until the development of vaccines for masses, the only possible way of protection is to limit the interaction with the people and isolate the people by imposing full or smart lockdown. The efficient smart lockdown could be imposed by employing the track and trace method that only isolates the infected people and their contacts. For this purpose, several smartphone apps for android, iOS, and Windows operating systems have been developed for tracing, tracking, and informing citizens about whether they have recently come in close contact with the person showing confirmed attributes of COVID-19. These apps can be either private or government owned.
The contact tracing operates by identifying positive cases of COVID-19 and asking them for their close contacts manually or identifying their close contacts in an automated way. Fig. 1 presents the building block and working mechanism of the contact-tracing apps [1]. The contact-tracing apps exchange information when the phones of two persons are close enough to each other. These people who came socially close to one another will be informed if their counterparts during the social interaction were officially infected with the COVID-19. These apps can only serve as the anchor point to inform citizens and provide suggestions on whether they should go to isolation or not. These apps have already shown efficiency in controlling the spread of the virus in South Korea and Singapore and flatten the spread curve through “test” and then “trace” mechanism [2], [3].
Fig. 1.
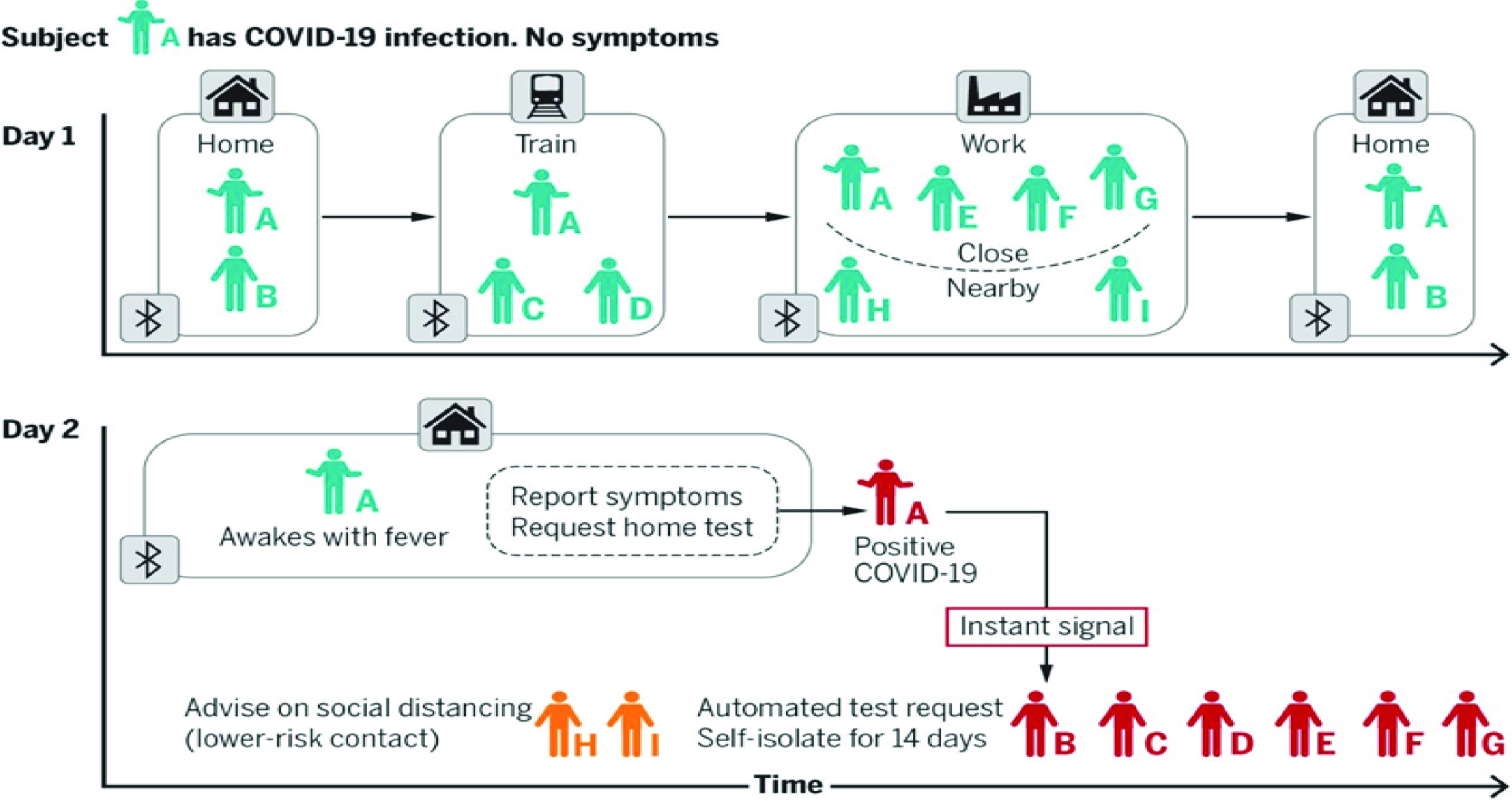
Tracing and isolating through smartphone-based contact tracing [1].
The contact-tracing apps are broadly developed by the national or country lead health regulators. To provide a reliable and efficient decision, the developed apps utilize the information from various smartphone sensors (GPS and Bluetooth) along with names, addresses, gender, age, contact details, calling log history, contact history, etc., to make the decision. These apps either interact automatically with the national health data system for the test results of the citizens or the citizens could manually provide test results to the health organization. For instance, upon downloading, Pakistan’s track and trace app1 requests permission to use the device’s location and user personal details, such as name, phone number, and email address, and that stored data will be shared with a third party. The current version of this app (as of June-2020) then uses the device’s location and the location of users with positive COVID-19 test results to render a map showing high-level hotspots for COVID-19 infections. Similarly, Google and Apple jointly developed an API that enables app developers to use the Bluetooth beacon messages for exchanging information between two persons who are in close contact with each other and showing virus symptoms. Some countries use the call detailed records to trace the close contact of the infected person and isolate them as well.
The use of these apps is normally voluntary and is considered as the support to control the spread of the virus. The developed app requests users for specific permission, e.g., contact details, call history, Web searches, camera permissions, access to call records, messages, and mobile media (videos and photographs). This information could pose serious privacy and security risks to the users and limit users to use these apps. The privacy of users may be protected through the use of different mechanisms, e.g., data anonymization, differential privacy, and decentralized app development [4]. However, it is already identified that anonymization systems are not providing effective privacy preservation [5]–[7], and decentralized app development is still at the early stage and progressing very slowly.
In this article, we provide a first look at the permission, security, and privacy analysis of the contact-tracing apps available at the Android and iOS app stores. We have studied app stores to define the nature of the privacy risks these apps have, what types of permissions these apps are requesting for their functioning, which permissions are unnecessarily required, and how they store and process the user data. Currently, only a small number of certified apps (developed by the country regulator) are available at the play stores, so we performed an exhaustive manual analysis on the available apps. Our analysis shows that the majority of the track and trace apps collect personal information, such as name, device ID, and location, however, some apps require access to further resources, such as SMS, microphone, camera, and storage memory of the device. Access to such resources is not required for the accurate function of such apps, and therefore, should not be requested by the developers. Furthermore, a number of apps disclose sharing data with third parties, however, a small number of these acquire the permission of the user before sharing this data with the third parties. As track and trace apps are voluntary and rely on the public’s trust to achieve their function effectively [8], addressing concerns with regards to data collection and sharing are paramount to their success to combat COVID-19.
The remainder of this article is organized as follows. Section II provides a discussion on privacy and permission analysis of mobile apps and work performed toward the development of track and trace apps. Section III defines the background on the trace and track smart applications. The section also provides the working mechanism and important features of developed apps. Section IV critically analyzes the security and privacy of different apps. Section V provides recommendations for design chose secure development and concludes this article.
II. Related Work
A large number of works have been presented that analyze the functionality of smartphone apps and the leakage of the sensitive information of their users [9]–[11]. Many contact-tracing applications involve tracing users using GPS, Bluetooth, and wireless technologies [12]–[17]. These approaches usually provide users with two options. Either the user has to self-report themselves or the application takes the help of a wireless technology [18]. A large number of people are currently downloading and using contact-tracing apps, and hence, the privacy aspects of these apps have become paramount for the research and development of unanimous privacy regulation. The regulators, such as the Federal Trade Commission, the U.S. National Telecommunication and information administrations, the European Union Commission [19], [20], and Information Commissioner’s Office [21] are analyzing and providing these guidelines to the app developers, content creators, and website operators to improve the development of their products in terms of security and privacy. In this section, we summarize works related to the security and privacy of smartphone apps.
Smartphone apps normally get access to user data and other information through the use of permission [22] that the users provide to the smartphone app at the time of app installation. For example, an app might ask to grant to see the location of the user, the messages stored on the mobile phone, the search history, etc. The user can still control the permission after installation but it might affect the functionality of apps’ operations. Providing permission to various private information would expose the private information of users to the advertisers and insurance companies [23], [24], and publicly expose personal data of the users without the user’s consent [25], [26]. A large number of smartphones’ app also ask unnecessary permission that is not required for the functionality of the app, these apps might pose a serious threat to the privacy and security of the users [27], [28]. Ikram and Kaafar [29] and Ikram et al. [30] analyzed the security and privacy of smartphone apps designed for blocking the advertisement and providing mobile VPN clients. Liccardi et al. [31] analyzed the permissions requested by the smartphone apps and assigned a sensitivity score to the app if the app asked to read the personal information of the users. They concluded that around 56% of the app asks users to provide permission to sensitive parts of the user’s data. Barrera et al. [32] investigated the relationship between free android apps and the most popular 1100 Android apps by deploying machine learning methods. It is also concluded that people are willing to use the paid version of smartphone apps if apps are not asking for unnecessary permissions. Enck et al. [33] proposed a lightweight certification mechanism to identify Android apps that are asking for suspicious permissions. Chia et al. [34] studied the user-consent permission systems by using the user-centric data from the Facebook apps, chrome browser extensions, and Android smartphone apps. It is very important to develop tools or applications that inform users about the privacy indicator of the apps they are using for specific purposes. To address this issue, Van Kleek et al. [35] developed a prototype that provides users with privacy indicators of the app. The prototype also identifies previously exposed hidden information flows out of the apps.
Contact tracing with smartphones can be employed to restrict the transmission of a pandemic disease. Utilizing computing technologies to avert and control the pandemic seems to be an obvious choice. However, these contact-tracing apps might invade privacy, collect personal data, and justify mass surveillance against users’ wishes. There must be a protocol for contact tracing that observes commitment to privacy, as well as provides the consent mechanism where there is a need to share individual data. Contact tracing may collect personal data such as location, which is not an effective privacy control when it comes to user’s data [36]. The process of contact tracing usually involves collecting users’ privacy information without informing them. Privacy-literate individuals might be reluctant to share their information, which in turn hampers the process of contact tracing. Privacy-preserving approaches might encourage individuals to participate more in this process and increase their confidence in those applications [18].
Prominent privacy researchers from across the world are arguing with the government agencies and vendors involved in developing the contact-tracing application about the privacy, and also highlighted the catastrophic consequences these apps would have on the citizen’s private lives [37], [38]. To ensure privacy, Cho et al. [39] utilized the semantics of private set interaction for assessing the risk exposure of users using encrypted and anonymous GPS locations. Shukla et al. [40] analyzed the privacy preservation mechanism for various contact-tracing applications and discussed the attributes which contact-tracing apps should have to ensure the privacy of users. Parker et al. [41] discussed the ethical consideration of contact-tracing apps for fighting against the COVID-19. Several contact-tracing application has been compared in [42] in terms of data collection, retention of data, purpose, and sharing of collected data, and what mechanisms the apps have deployed to ensure the privacy of users. Most recently, Troncoso et al. [4] described and analyzed a decentralized system for secure and privacy-preserving proximity tracing to combat the spread of COVID-19. The system is solely based on the anonymous identifiers of positive users of the COVID-19 without providing the exact location information to the health authorities. Vaudenay [43] analyzed the security and privacy properties of the pan-European decentralized privacy-preserving proximity tracing (DP3T) system. Health authorities or any other users would not be able to learn the private information of the users except a notification message when a person is exposed to COVID-19 affected person. Sun et al. [44] analyzed the security and privacy of contact-tracing apps in three dimensions: 1) evaluate the design choice (centralized or decentralized) used for privacy preservation; 2) static analysis for the identification of potential vulnerabilities; and 3) evaluate the robustness of approaches used for privacy preservation. The paper has not analyzed the permission analysis. Gvili [45] analyzed the security and privacy properties of Bluetooth-based specification by Apple and Google, concluding that the specifications may have some significant security and privacy risks. The Centers for Disease Control and Prevention (CDS) have issued guidelines that define a set of features a contact-tracing app should have to help health departments to overcome the COVID-19 pandemic [46].
III. Characterizing Contact-Tracing Apps
Contact tracing is an important tool for the community to prevent the outspread of novel pandemic diseases, such as COVID-19 [39]. In the past, contact-tracing tools have shown effectiveness against the spread of transmissible diseases, such as STD, HIV, Ebola, and tuberculosis [47], [48]. Contact tracing is the process of identifying persons who are in close contact with the infected person so that exposed targets can be informed to have self-isolation and quarantine, thus breaking the chain of transmission [36]. The current outbreak of COVID-19 and its highly contagious feature motivates technology developers to develop smartphone apps for the effective tracing of the footprint of the disease. In this section, we provide the architectural setup of contact-tracing apps and their significance toward controlling the spread of disease.
A. Centralized and Decentralized Architecture
The design of contact-tracing apps is mainly using data from the users thus has some privacy concerns that motivate the developer to come up with privacy-preserving solutions. The privacy of users can be addressed using the centralized and decentralized system setup. The centralized and decentralized apps entirely have different architecture and properties shown in Fig. 2 and explained as follows.
Fig. 2.
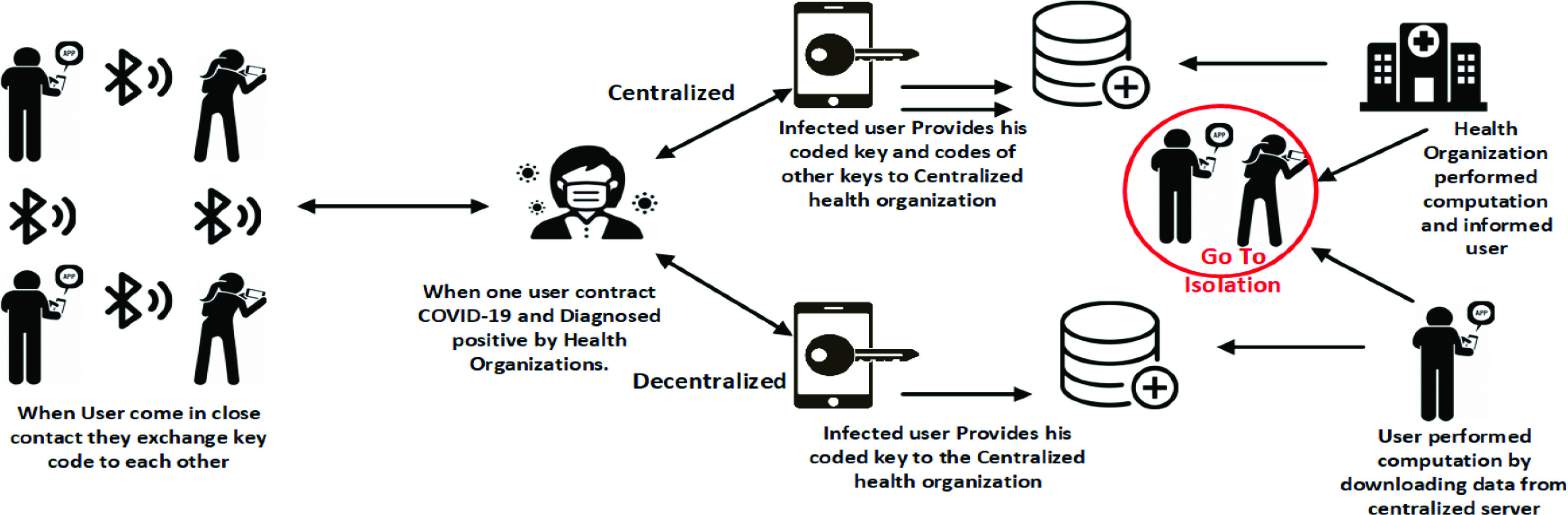
Architectural setup of contact-tracing apps.
1). Centralized Models:
In the centralized setup, the smartphones of the users having specific contact-tracing apps send the random identifier to the centralized trusted system. The centralized system in this setup holds the information from all users of the app. If a person has tested positive for the COVID-19 virus, the identifier of other users who have exchanged identifiers in the past can be sent to the centralized server along with other information, e.g., time data are sent, a time when identifiers are exchanged, etc. The centralized system decrypts the identifiers and automatically notifies the interacted phones suggesting or informing users to self-isolate or take other preventive measures. The centralized system can also utilize the available information for further analysis and policies for placing lockdown in hard-hit proximities.
2). Decentralized Models:
In the decentralized setup, there is not a trusted centralized system that exists for the handling of the user’s data and matching of the smartphone’s identifier. If a person is diagnosed positive with the COVID-19, the identifier of his phone and test result is uploaded to the centralized system. Other smartphones having the app can access these reports and locally establish the truth whether he was close to an infected individual or not. If a smartphone comes across the identity that has COVID-19, then an alert is sent to the user of the smartphone for precaution and self-isolation. The location and proximity of the person are not known to the centralized system, thus ensuring the privacy of the users using the app. The health organizations or the government still used the shared data to understand the spread of the virus in the community but would not have detailed information about the users.
B. Significance of Contact Tracing for COVID-19
Since the outbreak of the COVID-19 pandemic in December 2019, as of June 2020, there exists no medicine or vaccine to fight against the rapidly spreading pandemic. Governments across the world are currently focusing on the ways that would have the least load on their health systems. This has been achieved through imposing travel restrictions or lockdown, however, it is not only affecting the economy but there are also fears of the second wave of infection once the restrictions are relaxed. The governments are finding ways to identify the methods for contact tracing in order to quickly identify and isolate the infected persons. The manual contact tracing is not only slow and has a late response but would also require resources for identifying infected persons and then asking for his contacts and then contacts of his contacts to track the flow of the disease. The technologies soon realized the importance of smartphones and used the inbuilt smartphone sensors for tracking in an automated and efficient way. The use of digital technologies helps the citizen at the early stage of the virus spread and inform people for isolation at the early stage. The use of smartphone apps for contact tracing has shown promising results in several countries to combat the spread of the virus [49], however, the performance efficiency depends on the number of people using the application [50]. One thing that limits the usage of the app is the privacy because a large number of existing apps store data at the central trusted system, and in some circumstance, these data are made available to the third-party systems for performing artificial Intelligence and data analysis.
C. Vendor Support
As the healthcare officers and medical entities are working together worldwide to fight the spread of this pandemic, Google and Apple have joined an effort and developed a privacy-preserving contact-tracing API that uses Bluetooth signals [51] for exchanging information between people who are in close contact with each other. The apps using this API operate in a decentralized fashion, however, a centralized database is maintained. This framework allows healthcare agencies to propose or develop smartphone apps that help in limiting the spread of the disease with the help of Bluetooth technology. This API will bring interoperability between iOS and Android devices while maintaining privacy, consent, and transparency [52]. A test project, private automated contact tracing (PACT), was built at MIT to harness the strength of Bluetooth-based, privacy-preserving, automated contact-tracing API. This project detects proximity between contacts with the help of Bluetooth signals within a 6-foot radius. Instead of relying on the GPS, this system sends out random Bluetooth numbers, which can later be updated to a database with the user’s consent [53]. The first large-scale pilot for this joint venture has been launched in Switzerland, known as SwissCovid. This application determines the close contact that lasted for more than 15 min and notifies the user with the procedure to follow [54].
Apple also released a new application for COVID-19 based on CDC guidelines that provide COVID-19 information across the USA. In this application, the users have to answer some questions related to recent exposure and risk factors. In return, they get a CDC recommendation on what their next step should be. However, this application does not replace a healthcare worker in any way [55], [56]. Another application, “HEALTHLYNKED COVID-19 Tracker,” which became the most downloaded coronavirus tracker application for March. The application enables users to track local cases and chat with other users around the world. The most unique feature of this application is that it enables real-time chat with other users and share updates [57], [58].
IV. Analysis of Contact-Tracing Apps
In this section, we present our approach for studying current contact-tracing apps for COVID-19. We have focused on smartphone apps for any platform (iOS, Android, and Microsoft) and available anywhere in the world. Although there appears a concerted effort by governments across the globe to contain the pandemic, we identified through our analysis that many such apps have been developed by third-party individuals or organizations. Therefore, we have also included these in our analysis. Furthermore, as the contact-tracing technology is still in its early stages (especially within the context of COVID-19), although many apps claim to perform track and trace function, their effectiveness in this respect is subjective.
A. Data Collection
In order to achieve an in-depth analysis of current track and trace apps, we performed exhaustive search techniques to collect relevant apps across two major platforms (iOS and Android), irrespective of the country or the developing organization (government and private). We have chosen iOS and Android because these systems currently hold the most market share in the smartphone industry. Specifically, we used keywords, such as COVID-19, COVID track and trace, and Coronavirus track and trace. We analyzed the results of our search queries to filter apps that did not relate to contact tracing to mitigate the spread of COVID-19. We used a manual analysis of the app description to conduct this filtering. Furthermore, as several countries have encountered difficulties to achieve effective contact tracing, we did not exclude apps performing the partial or limited function in this regard. Overall, we identified 26 smartphone apps that claim to perform contact tracing in their description belonging to 17 different countries. The details of these apps are presented in Table I with a brief description of some apps presented below. Furthermore, Fig. 3 presents a graphical representation of the timeline with respect to launching dates of prominent apps.
-
1)
COVID-19 Gov PK is an app developed by the government of Pakistan. Initially, the application provided awareness to citizens about COVID-19, however, with the development of the new radius alert feature, this application provides information that is hot-spot areas that help the country to impose smart lockdown [59].
-
2)
Health Canada is developed by the government of Canada to provide a personalized recommendation to the users based on their risk factors. Personal data collected is only used by Health Canada and is not shared with any other application or agency [60].
-
3)
The government of Vietnam has developed an application named COVID-19, which includes features, such as chatbot, consultation, and live updates on COVID-19. The application requires access to media, location, storage, device ID, and call logs. The application’s privacy policies are updated in its native language [61].
-
4)
COVID19—DXB Smart App is developed by the government of Dubai and provides general information on COVID-19 and also provides correct statistics. The application collects personal information voluntarily but does not share with the third-party applications unless required by the law [62].
-
5)
COVI is a third-party COVID-19 informative app developed by Droobi, a Qatar-based digital company. This application collects personal data, such as contact information, age, health information, unique identifiers, etc. [63].
-
6)
Corona360 is an app developed in South Korea that enables users to update their COVID-19 status as well as view the status of other people. For privacy reasons, the app does not collect any personal information, such as ID, name, or phone number [64].
-
7)
CoronaCheck is a third-party application that has been developed to enable its users to conduct self-assessment and provide accurate expert COVID-19 information to the users. This application does not collect any personal information and does not share data with third-party vendors [65].
-
8)
The Beat COVID Gibraltar app is developed for the region of Gibraltar and it utilizes Bluetooth technology in a decentralized way to track other phones who come in close contact with the person declared himself as the virus affected.
-
9)
BC COVID-19 Support is developed for the resident of British Columbia, Canada, to inform the people about the status of COVID-19 in British Columbia and guide them on what next action people should take. All the recommendations are personalized so it involves some level of contact tracing.
-
10)
COVID Symptom Study has been designed for everyone to report their health status to the people who are developing policies to fight against the Virus.
-
11)
BeAware Bahrain is a mobile application developed for the region of Bahrain that helps citizens to contain the spread of the virus by using the contact-tracing efforts.
-
12)
Tawakkalna (Covid-19 KSA) is the official app of the kingdom of Saudi Arabia. It helps in controlling the spread of COVID-19 and suggests authorities where to impose the curfew and lockdown.
TABLE I. Analysis of Smartphone Apps Designed to Limit the Spread of COVID-19.
| App | Platform | Permissions Requested | Privacy Policy | Country | No of Downloads | TLS/ SSL | App Reviews | App version | API version |
|---|---|---|---|---|---|---|---|---|---|
| COVID-19 Gov PK | Android | Location (approximate and precise), full network access, prevent device from sleeping | Data to be shared with third party | Pakistan | 500,000+ | No | lack of encryption. Data might be traveling in plaintext. Radius alert is not accurate. Doesn’t show patients infected with COVID-19 | 3.0.7 | 5.0 and up |
| COVID Symptom Tracker | Android & iOS | Wifi connection information, full network access, audio settings, run at startup, prevent the device from sleeping | Collects sensitive personal information such as DOB, name, gender, COVID-19 tests status, location, details of any treatment, email, phone number, IP address. Shared with universities, research centers, amazon web service, google analytic, etc. | United Kingdom | 500,000+ | N/A | basic information related to COVID-19 symptoms, helps people take precautionary measures to self-isolate | 0.14 | 5.0 and up |
| BC COVID-19 Support | Android & iOS | Location (approximate and precise), full network access, prevent the device from sleeping | Personal information collected for COVID-19 alerts and management, only used by Ministry of Health | Canada | 10,000+ | Yes | Doesn’t update on a regular basis with current stats. No graph of active cases. Inaccurate and outdated information | 1.20.0 | 5.0 and up |
| OpenWHO: Knowledge for Health Emergencies | Android & iOS | Wifi connection, full network access, media/files, and storage, run at startup, prevent the device from sleeping | Requires name and email to create an account used for communications and the announcement of changes to the openWHO platform | United States | 500,000+ | No | Language issue to some people. Gives out a certificate for completing the course, increases public health knowledge | 3.4 | 5.0 and up |
| Pakistan’s National Action Plan for COVID-19 | Android | This application requires no special permissions to run | No information being shared | Pakistan | 50,000+ | Yes | Shares information related to COVID-19 and SOPs that government has launched for the safety of people | 1.1 | 5.0 and up |
| Health Monitoring PDMA | Android | Location (approximate and precise), receives data from internet and full network access | Information will be accessed by Smart Asset Sindh Health, shared with third party | Pakistan | 1000+ | No | Data information being sent in plaintext. No encryption or algorithm is used for data protection. Too many bugs. Doesn’t work efficiently. | 1.4 | 4.0.3 and up |
| Canada COVID-19 | Android | Location (approximate and precise), full network access, prevent device from sleeping | Personal data is collected by Health Canada only to support COVID-19. | Canada | 50,000+ | Yes | App doesn’t take into account pre-existing conditions. Will be much more effective if user can see map with active cases. | 4.0.0 | 5.0 and up |
| COVID-19 | Android | Location, phone, media, storage, camera, microphone, wifi, device ID, call information, download files without notification, run at startup, prevent the device from sleeping | May use personal information with third party | Vietnam | 100,000+ | N/A | App is only available for Veitnamese and not available in English. Very narrow coverage overall. Provides basic information. Only accessible in Veitnam | 1 | 4.4 and up |
| COVI | Android | Location, phone, wifi, device ID, call information, pair with Bluetooth devices, receive data from Internet, run at startup, prevent device from sleeping | Information such as DOB, name, the account number is collected and shared with trusted third parties | Qatar | 10,000+ | N/A | Only restricted for the people living in Qatar. Doesn’t get updates. Provides basic information | 2.0.2.2 | 5.1 and up |
| COVID19 - DXB Smart App | Android | Microphone, camera, location, storage, calendar, Wifi connection, media, receive data from Internet, pair with Bluetooth devices, full network access, prevent device from sleeping, change audio settings | Sends personal information such as ID, name, DOB, email, geographical location to a third party | Dubai | 1000+ | N/A | Only restricted for the people living in Dubai. Some users reported experiencing network error whenever they open this app | 3.8 | 5.0 and up |
| Corona 360 | Android | Location (approximate and precise), receives data from the internet, full network access, prevent the device from sleeping | Collects personal and sensitive data of user but whenever the data is being used, the user is notified for the reason | South Korea | 10+ Yes | Useful and multilingual solution for find Corona free locations | 2.2.2 | 4.3 and up | |
| CoronaCheck | Android &iOS | Full network access | Will not share any information | Pakistan | 10,000+ | Yes | Gives detailed information related to COVID-19 protection, symptoms. Translate English to Vocal language. | 1.1 | 4.1 and up |
| Coronavirus Australia | Android &iOS | Location (approximate and precise), receives data from internet and full network access | Collects information but does not use it without asking from the user | Australia | 500,000+ | N/A | App opens in the web browser which is clunky, the infection status is updated less often than the press releases, and is out of date later in the day. | 1.4.5 | 6.0 and up |
| NHS App | Android & iOS | Location, phone, media, storage, camera, microphone, Wifi, device ID, call information, download files without notification, run at startup, prevent device from sleeping | No specific information about sharing data with third parties | United Kingdom | 500,000+ | N/A | Requires personal details such as photo, name, DOB, NHS number. Requires 12 hours for the initial setup. Misleading/inaccurate information about compatible operating systems | 1.36.3 | 5.0 and up |
| Aarogya Setu | Android | Location (approximate and precise), receives data from internet and full network access | Cannot access its privacy policy | India | 50,000,000+ | N/A | Location, network and Bluetooth visibility required. No proper tracking, no radius alert, bugs, doesn’t update cases. Takes a new location every time when accessed | 1.4.1 | 5.0 and up |
| TraceTogether | Android & iOS | Media, storage, receive data from Internet, pair wth Bluetooth devices, full internet access, prevent device from sleeping | Mobile number and anonymous ID are shared in a secure server and not available to be shared with Public | Singapore | 500,000+ | N/A | Doesn’t alert you to infected cases in your area. Drains battery pretty fast due to Bluetooth connection. | 2.2.0 | 5.1 and up |
| HaMagen | Android &iOS | Device and app history, location, Wifi connection, full network access, prevent device from sleeping, change network connectivity | Cross-referencing location data with the corona patients | Israel | 1,000,000+ | No | Correlates overlaps only since installation. Should extract and use historical information. Data processed locally when a user opts against downloaded ”Corona paths” | 2.2.6 | 5.0 and up |
| Home Quarantine (Kwarantanna domowa) | Android & iOS | Location, phone, media, storage, camera, microphone, wifi, device ID, call information, download files without notification, run at startup, prevent device from sleeping | Collected data may be shared with third party | Poland | 100,000+ | N/A | GPS location is invalid. Cannot add a phone number as it gives away error. | 1.39.5 | 6.0 and up |
| NHS 24: COVID-19 | Android & iOS | Full network access, receives data from internet prevent device from sleeping | Collect personal data and share with third party | UK | 1000+ | N/A | Not Compatible Basic information only | 1.0.3 | 4.1 and up |
| Beat Covid Gibraltar | Android | view Wi-Fi connection,pair with Bluetooth devices, full network access | No personal data will be stored or used | Gibraltar | 10000+ | N/A | Developed only for Gibraltar, easy to use | 1.18 | 6 and up |
| EHTERAZ | Android | location data, phone access for calls, Photos / Media / Files, full network access | personal data will be stored or used | Qatar | 1,000,000+ | n/A | additional authentication performed, some privacy flaws are identified | 9.02 | 6 and up |
| BeAware Bahrain | Android | require access to apps running, read calendar information, require access to location, media files, and storage, pair Bluetooth devices | personal data will be stored or used | Bahrain | 100,000+ | N/A | some privacy flaws are identified | 0.2.1 | 4.4 and up |
| Shlonik | Android | record audio, access to running apps, require access to location, media files, and storage, pair Bluetooth devices, precise location information, full network access | Collects data and location information | Kuwait | 100,000+ | N/A | some privacy flaws are identified | varies | 4.4 and up |
| COVID Radar | Android/iOS | phone access, access to media files and storage, pair Bluetooth devices | Data is provided by users manually | Netherlands | 50,000+ | N/A | N/A | 1.1.2 | 6 and up |
| Tawakkalna (Covid-19 KSA) | Android | GPS Location, read the storage data, take pictures and make video, pair via Bluetooth device, full network access | Data is provided by users manually | Saudi Arabia | 1,000,000+ | N/A | helps in imposing curfew | 1.7 | 6 and up |
| MySejahtera | Android | precise location (GPS and network-based), call access, media & storage access, camera access, full network access | Data is provided by users manually | Malaysia | 1000K+ | N/A | user also need to register through their website | 1.0.24 | 4 and up |
Fig. 3.
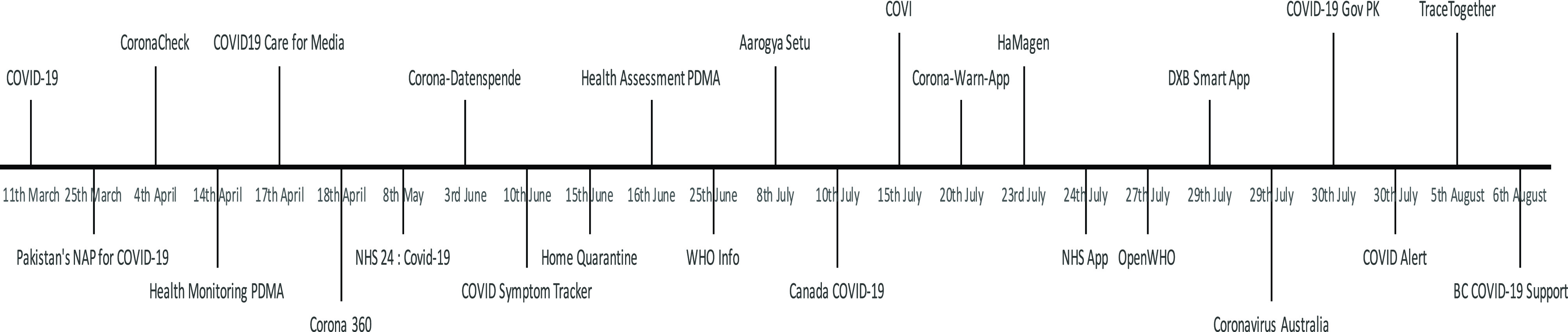
Timeline for release of COVID-19 track and trace apps.
Our study of these apps consisted of analyzing publicly available information shared by the app developers and platform, i.e., privacy policy, permissions requested, and user reviews. Furthermore, as some of the apps did not use SSL, we performed black-box testing of the apps using the Burp suite to analyze the network traffic during the app usage. The traffic analysis did indeed help us identify the information collected by these apps and shared with back-end servers that are liable to interception using network sniffing software.
B. Permission Analysis
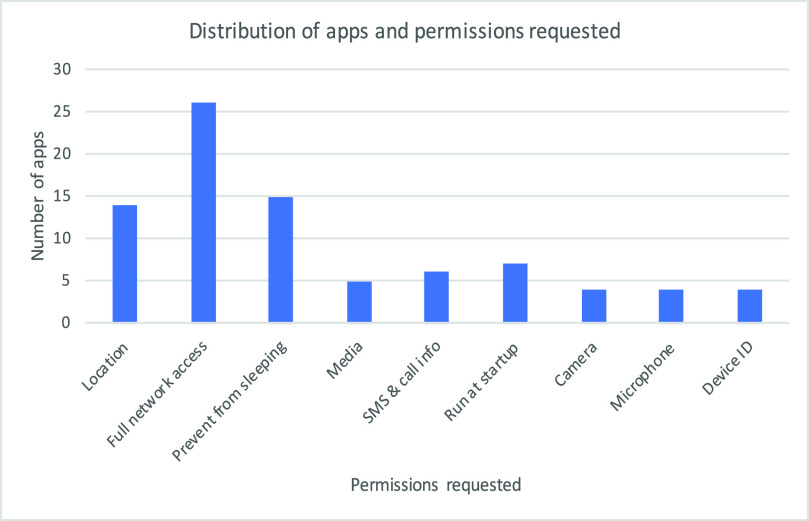
Permissions required by a smartphone app are significant as they communicate with the user the resources required by the app to perform its function. Therefore, presenting the user with a list of permissions not only achieves transparency (providing the user an insight into the app operation) but it also serves to seek user consent. Within the context of our study, we have gathered information about the permissions required by the track and trace apps under study. Fig. 4 presents a graphical representation of the distribution of the apps with respect to permissions required by them.
Fig. 4.
Distribution of apps and requested permissions.
As presented in Fig. 4, we expected the majority of the apps to require access to location data of a device, however, our study also identified permissions requested by the apps that are not necessary to perform their function. For instance, we identified 06 apps that require access to SMS and call information of the device. In some scenarios, access to phone numbers can be envisioned, however, access to SMS within a device is not essential to the function of a track and trace app. Similarly, we identified 04 apps that require access to the camera of the device which is of course an unexpected request by a track and trace app.
Furthermore, 04 apps studied require access to the microphone of the device, whereas 05 apps require access to media and storage of the device that are of course not critical to the app’s function. Such apps are indeed causing concern regarding the privacy of their users and exemplify a lack of attention to the security and privacy of the users by app developers.
C. Analyzing Privacy
To understand the privacy considerations applied for the apps within our study, our analysis took into account the privacy policy published by the application developer as well as the use of basic privacy protection mechanisms such as SSL/TLS to achieve encrypted data transmissions.
Through the study of privacy policies of the apps as well as traffic analysis, we identified that most of the apps collect personal data, such as location information, name, phone number, etc. Although collecting such information is vital for effective track and trace, appropriate mechanisms should be applied to ensure secure sharing, processing, and storage of such data. Such details were not available for most of the apps analyzed in this study. Furthermore, an interesting observation we made was the type of information gathered by the apps. Specifically, our analysis identified that the track and trace app developed by Dubai collects personal information, such as date of birth, name, email address, and caller ID. Such information is not required for effective track and trace and risks the privacy of users as any malicious actor with access to such information can easily perform ID theft attacks. We believe data collection policies for such apps require immediate attention to minimize the risk to individual user privacy.
A significant challenge with respect to security and privacy within smartphone apps is sharing data with third parties to aid targeted advertisements. Smartphone apps using such strategies leverage advanced analytics techniques to identify user behavior and profiles to achieve personalized advertisements. Within this context, the information collected by track and trace apps is highly personalized and if made accessible to third-parties can lead to sophisticated advertisement techniques breaching public trust and confidence in such apps. Our analysis of the apps concluded that all apps are free to use and do not include any in-app advertisements. However, some apps (as highlighted in Table I) do share data with third parties without precise information about who these third parties, what data are shared, and how this data will be used by the third parties. Therefore, focused efforts from the research community are required to enhance data sharing, processing, and storage practices within such scenarios.
Another aspect concerning the privacy of information collected is how it is stored and shared by the apps. In this respect, our analysis revealed that ten of the apps shared data with third parties, however, the nature and identity of such parties are not identified in the privacy policies. This is a cause of concern regarding individual privacy as the aims of sharing this data are not clear and therefore, users are not aware of how their data may be used. For instance, a common apprehension among users is the sharing of data with advertisement agencies who may wish to use such data for targeted advertisement and adware.
Having said this, we also identified examples of good practice within our analysis. Specifically, some of the apps clearly state requirements for user consent before sharing data with third parties, thereby assuring users with respect to how their data are shared. For instance, Corona360 (the app developed by the government of South Korea) collects the personal and sensitive data of users but whenever the data are used, the user is notified for the reason of data usage.
In addition to the above, our analysis also uncovered security vulnerabilities within some apps. In particular, we identified five apps that were not using SSL/TLS to ensure secure communication made through the app. Pursuing this direction of analysis, we conducted traffic monitoring of such apps and identified serious flaws in the app developed by the government of Pakistan. The details of these vulnerabilities have been reported to the relevant authorities, however, such vulnerabilities do put user privacy at risk, especially where the app is collecting and utilizing personal user data.
D. App Review Analysis
In addition to the permissions requested, privacy policy, and traffic analysis of the worldwide COVID-19 track and trace apps, we have also studied user comments available in Google Play and App Store reviewing these apps. Although the majority of these comments are related to the usability and general function of the app, we found some comments to be insightful with respect to how the app collects and utilizes data. For instance, the app developed by the government of Israel was commented by a user to ask for users’ permission when sharing data with third parties as well as to guarantee not to send the data anywhere but compare it locally on the user’s device against downloaded “Corona paths.” Another interesting observation was made for the Corona-Datenspende app, where user comments suggest that one cannot use the app without connecting to a fitness account and hence completely breaking the point of anonymity. As suggested by the user, connecting to the app via a fitness app such as Fitbit indeed does indicate sharing personal user data across different apps, which is a risk to user privacy.
Through analysis of the user reviews of apps, we observed that although some of the users have included concerns about the privacy of information through their feedback, these are relatively minor proportions of users. For instance, for the COVID-19 Gov PK app, user review includes comments highlighting a lack of encryption and concerns about data traveling in plain-text. However, for apps such as Corona-Datenspende that requires a user to connect to a fitness app as a prerequisite, there are no user comments with regards to how data are captured, analyzed, stored, and processed between the third-party fitness app and the government app for COVID-19. These observations reflect a lack of awareness among users with regards to measures to preserve the privacy of personal data collected, stored, and analyzed by computing systems, therefore, requiring efforts to raise awareness among users.
V. Conclusion and Recommendations
As the Coronavirus is a contagious disease that spreads through close social interaction between humans, contact tracing is vital for containing its spread. Mobile devices present an ideal platform to introduce contact-tracing software due to their ease of use, widespread ownership, and personalized usage. Therefore, several smartphone apps have been developed by governments, international agencies, and other parties to mitigate the virus spread. However, there is an increasing concern regarding the collection and use of data, and outsourcing data to third-party systems. In this article, we analyzed a large set of contact-tracing apps with respect to different security and privacy metrics. Specifically, we analyzed contact-tracing apps for permission analysis, privacy analysis, the security of the apps, and reviews of the users. Our major findings are as follows.
-
1)
Although there have been significant technological advancements to aid COVID-19 response, contact-tracing apps require further enhancements to achieve desired objectives in a privacy-aware manner.
-
2)
A number of track and trace apps request permissions that may not be required for the successful operation of the app’s function. These include access to storage media, camera, and microphone, which might result in a breach of user’s privacy.
-
3)
Several apps mention outsourcing data to third parties, however, it is unclear who are these third parties, what data are shared, and how it is processed by these parties.
-
4)
Some apps (used in developing countries) have not adopted appropriate security measures for the exchange of the data to and from the user to the data centers.
-
5)
Our analysis of the user reviews and the ratings for contact-tracing apps suggested that a large number of users are aware of the privacy concerns of these apps.
Though digital technologies could play a prominent role in addressing the current pandemic challenges and the containment of the spread of the virus. However, the effectiveness and accuracy of these systems depend upon the working architecture of applications and user participation. The user participation could be improved if systems employed a mechanism that ensures the security and privacy of users. To ensure the privacy, security, and secure development of contact-tracing apps, we recommend the following design choices that should be followed for the development of contact-tracing apps.
-
1)
In order to ensure the privacy and security of the user data, the contact-tracing systems have to consider the well-established and state-of-the-art encryption systems for storing data, enable personalized access control mechanisms, and utilize secure communication mechanisms for the exchange of data between the users and the data center. Furthermore, developers should also consider the semantics of secure software development, strong authentication mechanism possibly two-factor authentication to minimize the risk of misuse.
-
2)
The contact-tracing apps should perform their operations in a completely decentralized way, i.e., the system performs the bulk of its operation at the user side.
-
3)
The app’s privacy policy should be mentioned in a way that a user could easily understand. The developer should also adopt the mechanisms that they could easily destroy user data once this pandemic is over.
-
4)
The design system should not unnecessarily seek permissions, for example, access to videos, browsing history, or the images.
-
5)
The developers should consider the measures that assign a unique pseudonymized identifier for the users that must not be linked to the user’s real identity and could not be used to learn the private information of users through background knowledge.
-
6)
To improve usability, the design should be simple and should have a user interface for interaction and personal tracking.
-
7)
We also recommend developers and regulators to use the identity verification (telephone number authentication) or authentication system within their trace and track system so the information could be exchanged through the reliable voice call.
It is very important to incorporate the techniques that ensure the privacy of citizens so that they can confidently participate in limiting the spread of the disease. The apps should not serve as the tool for mass surveillance tools so that people trust the system without having any concerns about their privacy and tracking of their private lives. As a part of our future work, we are looking to conduct a user study using qualitative measures focused on directly considering the feedback from users to further understand the usability and security concerns of users.
Footnotes
References
- [1].Ferretti L.et al. , “Quantifying SARS-CoV-2 transmission suggests epidemic control with digital contact tracing,” Science, vol. 368, no. 6491, 2020, Art. no. eabb6936. [Online]. Available: https:// science.sciencemag.org/content/368/6491/eabb6936 [DOI] [PMC free article] [PubMed] [Google Scholar]
- [2].(2017). Test, Trace, Contain: How South Korea Flattened Its Coronavirus Curve. [Online]. Available: https://tinyurl.com/yabnmckr
- [3].(2017). How Digital Contact Tracing Slowed COVID-19 in East Asia. [Online]. Available: https://tinyurl.com/tc8z8wj
- [4].Troncoso C.et al. , “Decentralized privacy-preserving proximity tracing,” 2020. [Online]. Available: https://arxiv.org/abs/2005.12273 [Google Scholar]
- [5].Narayanan A. and Shmatikov V., “De-anonymizing social networks,” in Proc. 30th IEEE Symp. Security Privacy, Berkeley, CA, USA, 2009, pp. 173–187. [Google Scholar]
- [6].Narayanan A. and Shmatikov V., “Robust de-anonymization of large sparse datasets,” in Proc. IEEE Symp. Security Privacy (SP), Oakland, CA, USA, 2008, pp. 111–125. [Google Scholar]
- [7].Sharad K. and Danezis G., “An automated social graph de-anonymization technique,” in Proc. 13th Workshop Privacy Electron. Society, 2014, pp. 47–58. [Online]. Available: https://doi.org/10.1145/2665943.2665960 [Google Scholar]
- [8].(2020). Coronavirus: NHs Contact Tracing App Needs 60% Take-Up to Be Successful, Expert Warns. [Online]. Available:https://tinyurl.com/y7u3mh7a
- [9].Au K. W. Y., Zhou Y. F., Huang Z., and Lie D., “Pscout: Analyzing the android permission specification,” in Proc. ACM Conf. Comput. Commun. Security, 2012, pp. 217–228. [Online]. Available: https://doi.org/10.1145/2382196.2382222 [Google Scholar]
- [10].Enck W.et al. , “TaintDroid: An information-flow tracking system for realtime privacy monitoring on smartphones,” in Proc. 9th USENIX Conf. Oper. Syst. Design Implement., 2010, pp. 393–407. [Google Scholar]
- [11].Shi L., Fu J., Guo Z., and Ming J., “‘Jekyll and hyde’ is risky: Shared-everything threat mitigation in dual-instance apps,” in Proc. 17th Annu. Int. Conf. Mobile Syst. Appl. Serv., 2019, pp. 222–235. [Online]. Available: https://doi.org/10.1145/3307334.3326072 [Google Scholar]
- [12].Altuwaiyan T., Hadian M., and Liang X., “EPIC: Efficient privacy-preserving contact tracing for infection detection,” in Proc. IEEE Int. Conf. Commun. (ICC), Kansas City, MO, USA, 2018, pp. 1–6. [Google Scholar]
- [13].Danquah L. O.et al. , “Use of a mobile application for ebola contact tracing and monitoring in northern sierra leone: A proof-of-concept study,” BMC Infect. Dis., vol. 19, p. 810, Sep. 2019. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [14].Prasad A. and Kotz D., “ENACT: Encounter-based architecture for contact tracing,” in Proc. ACM Workshop Phys. Anal. (WPA) Jun. 2017, pp. 37–42. [Google Scholar]
- [15].Reddy E., Kumar S., Rollings N., and Chandra R., “Mobile application for dengue fever monitoring and tracking via GPS: Case study for Fiji,” Mar. 2015. [Online]. Available: https://arxiv.org/abs/1503.00814 [Google Scholar]
- [16].Shahabi C., Fan L., Nocera L., Xiong L., and Li M., “Privacy-preserving inference of social relationships from location data: A vision paper,” in Proc. 23rd SIGSPATIAL Int. Conf. Adv. Geograph. Inf. Syst., 2015, pp. 1–4. [Online]. Available: https://doi.org/10.1145/2820783.2820880 [Google Scholar]
- [17].Yoneki E. and Crowcroft J., “EpiMap: Towards quantifying contact networks for understanding epidemiology in developing countries,” Ad Hoc Netw., vol. 13, pp. 83–93, Feb. 2014. [Google Scholar]
- [18].Hekmati A., Ramachandran G., and Krishnamachari B., “CONTAIN: Privacy-oriented contact tracing protocols for epidemics,” 2020. [Online]. Available: https://arxiv.org/abs/2004.05251 [Google Scholar]
- [19].(2017). General Data Protection Regulation GDPR. [Online]. Available: https://gdpr-info.eu/
- [20].(2017). Mobile Privacy Principles Promoting Consumer Privacy in the Mobile Ecosystem. [Online]. Available: https://tinyurl.com/yaxy74wa
- [21].(2017). Mobile Privacy Disclosures: Building Trust Through Transparency: A Federal Trade Commission Staff Report. [Online]. Available: https://tinyurl.com/y765bgxj
- [22].Felt A. P., Greenwood K., and Wagner D., “The effectiveness of application permissions,” in Proc. 2nd USENIX Conf. Web Appl. Develop., 2011, p. 7. [Google Scholar]
- [23].(2017). Many Popular Android Apps Leak Sensitive Data, Leaving Millions of Consumers at Risk. [Online]. Available: https://tinyurl.com/yb7hfjxr
- [24].(2017). Researchers Spot Thousands of Android Apps Leaking User Data Through Misconfigured Firebase Databases. [Online]. Available: https://tinyurl.com/ybjdrcth
- [25].Krishnamurthy B. and Wills C. E., “On the leakage of personally identifiable information via online social networks,” in Proc. 2nd ACM Workshop Online Soc. Netw., 2009, pp. 7–12. [Online]. Available: https://doi.org/10.1145/1592665.1592668 [Google Scholar]
- [26].Zuo C., Lin Z., and Zhang Y., “Why does your data leak? Uncovering the data leakage in cloud from mobile apps,” in Proc. IEEE Symp. Security and Privacy (SP), San Francisco, CA, USA, 2019, pp. 1296–1310. [Google Scholar]
- [27].Kang J., Kim D., Kim H., and Huh J. H., “Analyzing unnecessary permissions requested by android apps based on users’ opinions,” in Information Security Applications, Rhee K.-H. and Yi J. H., Eds. Cham, Switzerland: Springer, 2015, pp. 68–79. [Google Scholar]
- [28].Peddinti S. T.et al. , “Reducing permission requests in mobile apps,” in Proc. Internet Meas. Conf., 2019, pp. 259–266. [Online]. Available: https://doi.org/10.1145/3355369.3355584 [Google Scholar]
- [29].Ikram M. and Kaafar M. A., “A first look at mobile ad-blocking apps,” in Proc. IEEE 16th Int. Symp. Netw. Comput. Appl. (NCA), Cambridge, MA, USA, 2017, pp. 1–8. [Google Scholar]
- [30].Ikram M., Vallina-Rodriguez N., Seneviratne S., Kaafar M. A., and Paxson V., “An analysis of the privacy and security risks of android VPN permission-enabled apps,” in Proc. Internet Meas. Conf., 2016, pp. 349–364. [Online]. Available: https://doi.org/10.1145/2987443.2987471 [Google Scholar]
- [31].Liccardi I., Pato J., and Weitzner D. J., “Improving user choice through better mobile apps transparency and permissions analysis,” J. Privacy Confidentiality, vol. 5, no. 2, p. 1, Feb. 2014. [Online]. Available: https://journalprivacyconfidentiality.org/index.php/jpc/article/view/630 [Google Scholar]
- [32].Barrera D., Kayacik H. G., van Oorschot P. C., and Somayaji A., “A methodology for empirical analysis of permission-based security models and its application to android,” in Proc. 17th ACM Conf. Comput. Commun. Security, 2010, pp. 73–84. [Online]. Available: https://doi.org/10.1145/1866307.1866317 [Google Scholar]
- [33].Enck W., Ongtang M., and McDaniel P., “On lightweight mobile phone application certification,” in Proc. 16th ACM Conf. Comput. Commun. Security, 2009, pp. 235–245. [Online]. Available: https://doi.org/10.1145/1653662.1653691 [Google Scholar]
- [34].Chia P. H., Yamamoto Y., and Asokan N., “Is this app safe?: A large scale study on application permissions and risk signals,” in Proc. 21st Int. Conf. World Wide Web, 2012, pp. 311–320. [Online]. Available: https://doi.org/10.1145/2187836.2187879 [Google Scholar]
- [35].Van Kleek M., Liccardi I., Binns R., Zhao J., Weitzner D. J., and Shadbolt N., “Better the devil you know: Exposing the data sharing practices of smartphone apps,” in Proc. CHI Conf. Hum. Factors Comput. Syst., 2017, pp. 5208–5220. [Online]. Available: https://doi.org/10.1145/3025453.3025556 [Google Scholar]
- [36].Yasaka T., Lehrich B., and Sahyouni R., “Peer-to-peer contact tracing: Development of a privacy-preserving smartphone app,” JMIR Mhealth Uhealth, vol. 8, Apr. 2020, Art. no. e18936. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [37].(2017). Joint Statement on Contact Tracing: Date 19th April 2020. [Online]. Available: https://tinyurl.com/ybm27jxx
- [38].(2017). Contact Tracing in the Real World. [Online]. Available: https://tinyurl.com/ty7sxo5
- [39].Cho H., Ippolito D., and Yu Y. W., “Contact tracing mobile apps for COVID-19: Privacy considerations and related trade-offs,” 2020. [Online]. Available: https://arxiv.org/abs/2003.11511 [Google Scholar]
- [40].Shukla M., Rajan M. A., Lodha S., Shroff G., and Raskar R., “Privacy guidelines for contact tracing applications,” 2020. [Online]. Available: https://arxiv.org/abs/2004.13328 [Google Scholar]
- [41].Parker M. J., Fraser C., Abeler-Dörner L., and Bonsall D., “Ethics of instantaneous contact tracing using mobile phone apps in the control of the COVID-19 pandemic,” J. Med. Ethics, vol. 46, no. 7, pp. 427–431, 2020. [Online]. Available: https://tinyurl.com/ybojkjr8 [DOI] [PMC free article] [PubMed] [Google Scholar]
- [42].(2017). Privacy & Pandemics: The Role of Mobile Apps (Chart). [Online]. Available: https://tinyurl.com/ycyw9tpk
- [43].Vaudenay S., “Analysis of dp3t,” Cryptol. ePrint Archive, Lyon, France, Rep. 2020/399, 2020. [Online]. Available: https://eprint.iacr.org/2020/399 [Google Scholar]
- [44].Sun R., Wang W., Xue M., Tyson G., Camtepe S., and Ranasinghe D., “Vetting security and privacy of global COVID-19 contact tracing applications,” 2020. [Online]. Available: https://arxiv.org/abs/2006.10933 [Google Scholar]
- [45].Gvili Y., “Security analysis of the COVID-19 contact tracing specifications by Apple inc. and Google inc,” Cryptol. ePrint Archive, Lyon, France, Rep. 2020/428, 2020. [Online]. Available: https://eprint.iacr.org/2020/428 [Google Scholar]
- [46].(2017). Preliminary Criteria for the Evaluation of Digital Contact Tracing Tools for COVID-19. [Online]. Available: https://tinyurl.com/y7nroqlw
- [47].Sacks J. A.et al. , “Introduction of mobile health tools to support ebola surveillance and contact tracing in guinea,” Global Health Sci. Pract., vol. 3, pp. 646–659, Dec. 2015. [DOI] [PMC free article] [PubMed] [Google Scholar]
- [48].Armbruster B. and Brandeau M., “Contact tracing to control infectious disease: When enough is enough,” Health Care Manag. Sci., vol. 10, no. 4, pp. 341–355, Dec. 2007. [Online]. Available: https://tinyurl.com/y9yr4rry [DOI] [PMC free article] [PubMed] [Google Scholar]
- [49].Zhang B., Kreps S. E., and McMurry N., Americans’ Perceptions of Privacy and Surveillance in the COVID-19 Pandemic, Center Open Sci., Charlottesville, VA, USA, May 2020. [Online]. Available: https://ideas.repec.org/p/osf/osfxxx/9wz3y.html [DOI] [PMC free article] [PubMed] [Google Scholar]
- [50].Christophe F.et al. , Digital Contact Tracing: Comparing the Capabilities of Centralised and Decentralised Data Architectures to Effectively Suppress the COVID-19 Epidemic Whilst Maximising Freedom of Movement and Maintaining, Center Open Sci., Charlottesville, VA, USA, May 2020. [Online]. Available: https://ideas.repec.org/p/osf/osfxxx/9wz3y.html [Google Scholar]
- [51].(2020). Privacy-Preserving Contact Tracing. Accessed: May 29, 2020. [Online]. Available: https://www.apple.com/covid19/contacttracing
- [52].(2020). Apple and Google Partner on COVID-19 Contact Tracing Technology. Accessed: May 29, 2020. [Online]. Available: https://tinyurl.com/wfw9ojr
- [53].Scudellari M.. (2020). COVID-19 Digital Contact Tracing: Apple and Google Work Together as Mit Tests Validity. Accessed: May 29, 2020. [Online]. Available: https://tinyurl.com/y87sljrz [Google Scholar]
- [54].Leprince-Ringuet D.. (2020). The World’s First Contact-Tracing App Using Google and Apple’s API Goes Live. Accessed: May 29, 2020. [Online]. Available: https://tinyurl.com/y9on8x2u [Google Scholar]
- [55].(2020). Apple Releases New COVID-19 App and Website Based on CDC Guidance. Accessed: May 29, 2020. [Online]. Available: https://tinyurl.com/ya9mhzc8
- [56].(2020). COVID-19 Screening Tool. Accessed: May 29, 2020. [Online]. Available: https://www.apple.com/covid19/
- [57].(2020). Healthlynked Corp.’s COVID-19 Tracker No.1 Most Downloaded App in Apple Medical Store for March. Accessed: May 29, 2020. [Online]. Available: https://tinyurl.com/yafve87b
- [58].(2020). Healthlynked. Accessed: May 29, 2020. [Online]. Available: https://www.healthlynked.com/corona-virus-tracker/
- [59].Application Developed to Deal With Corona Virus, Ministry Electron. Inf. Technol., New Delhi, India, 2020. Accessed: May 29, 2020. [Online]. Available: https://tinyurl.com/y78gzc4v [Google Scholar]
- [60].(2020). Canada COVID-19. Accessed: May 29, 2020. [Online]. Available: https://www.thrive.health/covid19-collection-notice
- [61].(2020). COVID-19. Accessed: May 29, 2020. [Online]. Available: https://api.tetvietaic.com/pages/policye
- [62].(2020). COVID19—DXB Smart App. Accessed: May 29, 2020. [Online]. Available: http://csms.ae/PrivacyPolicy.html
- [63].(2020). Covi. Accessed: May 29, 2020. [Online]. Available: https://www.droobihealth.com/user-app/privacy
- [64].(2020). Corona360. Accessed: May 29, 2020. [Online]. Available: https://corona-360.com/
- [65].(2020). Coronacheck. Accessed: May 29, 2020. [Online]. Available: https://tinyurl.com/y8l4aq9z