Abstract
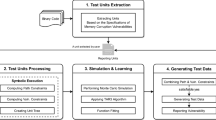
This paper considers various aspects of static analysis of C# programs in order to detect the maximum number of software bugs in an acceptable time. A complete cycle of software static analysis is described with the main focus being placed on the specifics of the C# language. Some methods are discussed that take into account popular features of C# at all levels of analysis: call graph and control flow graph construction, dataflow analysis, as well as context- and path-sensitive interprocedural analysis. A symbolic execution method is proposed, which is based on the works devoted to the Bounded Model Checking (BMC) and the Saturn Software Analysis Project. A memory model is described that enables an accurate intraprocedural analysis and allows one to create compact representations of error conditions associated with functions, which are essential for interprocedural analysis. A special attention is paid to the optimizations that occur during path-sensitive analysis of error conditions. The conditions need to be optimized in terms of size, because path-sensitive interprocedural analysis requires saving a large number of conditions for each analyzed function. The conditions are resolved using advanced SMT solvers (such as the Microsoft Z3 Prover). This paper also considers various approaches to modeling the behavior of library functions: based on a summary containing a set of properties required for analysis, or based on simplified implementations in C#. All the discussed solutions are implemented in the SharpChecker static analysis tool and are tested on a number of open-source projects from 1.5 thousand to 1.35 million lines of code.
Similar content being viewed by others
References
TIOBE Programming Community index. http://www. tiobe.com/tiobe_index
Microsoft Developer Network, LINQ (Language-Integrated Query). https://msdn.microsoft.com/ru-ru/ library//bb397926.aspx
Ivannikov, V.P., Belevantsev, A.A., Borodin, A.E., Ignat’ev, V.N., Zhurikhin, D.M., Avetisyan, A.I., and Leonov, M.I., Svace static analyzer for bug detection in program source code, Tr. Inst. Sistemnogo Program. Ross. Akad. Nauk, 2014, vol. 26, no. 1, pp. 231–250.
Coverity: software testing and static analysis tools. http://www.coverity.com/
Klocwork: source code analysis tools for security and reliability. http://www.klocwork.com.
SonarLint. http://www.sonarlint.org/
PVS-Studio for C/C++/C#. http://www.viva64.com/
Institute for System Programming, SharpChecker. http://sharpchecker.ispras.ru/ru/
Microsoft Developer Tools, Visual Studio. http:// www.visualstudio.com/ru-ru/visual-studio-homepage-vs.aspx
Roslyn. NET Compiler Platform. https://github.com /dotnet/roslyn
Aho, A.V., Lam, M.S., Sethi, R., and Ullman, J.D., Compilers: Principles, Techniques, and Tools, Addison Wesley, 2006, 2nd ed.
Sundaresan, V., Hendren, L., Razafimahefa, C., Vallee-Rai, R., Lam, P., Gagnon, E., and Godin, C., Practical virtual method call resolution for Java, Proc. 15th ACM SIGPLAN Conf. on Object-Oriented Programming, Systems, Languages, and Applications (OOPSLA), New York, 2000, pp. 264–280.
Falke, S., Merz, F., and Sinz, Ca., LLBMC: Improved bounded model checking of C programs using LLVM, Tools and Algorithms for the Construction and Analysis of Systems, Berlin: Springer, 2010, pp. 623–626.
Koshelev, V.K., Dudina, I.A., Ignat’ev, V.N., and Borzilov, A.I., Path-sensitive bug detection in C# programs by the example of null pointer dereference, Tr. Inst. Sistemnogo Program. Ross. Akad. Nauk, 2015, vol. 27, no. 5, pp. 59–86.
Andersen, H.R., An introduction to binary decision diagrams, 1997. Lecture notes, http://www.cs.utexas. edu/isil/cs389L/bdd.pdf
McMillan, K.L., Interpolants from Z3 proofs, Proc. Formal Methods in Computer-Aided Design (FMCAD), 2011, pp. 19–27.
Ecma International, ECMA-335 standard. http:// www.ecma-international.org/publications/ files/ECMA-ST/ECMA-335.pdf.
Mono Project, Mono.Cecil library. http://www.monoproject. com/docs/tools+libraries/libraries/Mono. Cecil/
Microsoft Developer Network, Windows API. https://msdn.microsoft.com/en-us/library/cc433218.
Microsoft Developer Network,.NET Framework class library. https://msdn.microsoft.com/ru-ru/library// mt472912(v=vs.110).aspx.
Author information
Authors and Affiliations
Corresponding author
Additional information
Original Russian Text © V.K. Koshelev, V.N. Ignatiev, A.I. Borzilov, A.A. Belevantsev, 2017, Trudy Instituta Sistemnogo Programmirovaniya, 2016, vol. 28, no 1, pp. 21–40.
Rights and permissions
About this article
Cite this article
Koshelev, V.K., Ignatiev, V.N., Borzilov, A.I. et al. SharpChecker: Static analysis tool for C# programs. Program Comput Soft 43, 268–276 (2017). https://doi.org/10.1134/S0361768817040041
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1134/S0361768817040041