Abstract
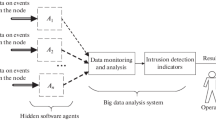
We have proposed an adaptive model of a system for detecting intrusions in a distributed computer network. The basis of the detection system consists of various data-mining methods that make it possible to classify network interaction as normal or anomalous using many attributes extracted from network traffic.
Similar content being viewed by others
References
DARPA Intrusion Detection Data Sets. http://www.ll.mit.edu/ideval/data.
Bhattacharyya, D.K. and Kalita, J.K., Network Anomaly Detection. A Machine Learning Perspective, CRC Press, 2014.
Platonov, V.V. and Semenov, P.O., Construction of an adaptive system for detecting network attacks, Sb. materialov 24 konferentsii “Metody i tekhnicheskie sredstva obespecheniya bezopasnosti informatsii” (Proc. 24th Conf. Methods and Technical Means of Information Security), St. Petersburg: Izd. politekh. univ., 2015, pp. 95–96.
Vapnik, V.N., The Nature of Statistical Learning Theory, Springer, 2000, 2nd ed.
Hsu, C.-W., Chang, C.-C., and Lin, C.-J., A Practical Guide to Support Vector Classification, Taipei: Department of Computer Science, National Taiwan University, 2003.
Aivazyan, S.A., Bukhshtaber, V.M., Enyukov, I.S., and Meshalkin, L.D., Prikladnaya statistika: Klassifikatsiya i snizhenie razmernosti: Sprav. izd. (Applied Statistics: Classification and Reduction of Dimension), Aivazyan, S.A., Ed., Moscow: Finansy i statistika, 1989.
Fodor, I.K., A Survey of Dimension Reduction Techniques, U.S. Department of Energy by University of California, Lawrence Livennore National Laboratory, 2002.
Zhambyu, M., Ierarkhicheskii klaster-analiz i sootvetstviya (Hierarchical Cluster Analysis and Matching), Moscow: Finansy i statistika, 1988.
Guha, S., Rastogi, R., and Shim, K., Cure: An efficient clustering algorithm for large databases, SIGMOD, 1998, vol. 27, pp. 73–84.
Author information
Authors and Affiliations
Corresponding author
Additional information
Original Russian Text © V.V. Platonov, P.O. Semenov, 2017, published in Problemy Informatsionnoi Bezopasnosti, Komp’yuternye Sistemy.
About this article
Cite this article
Platonov, V.V., Semenov, P.O. An adaptive model of a distributed intrusion detection system. Aut. Control Comp. Sci. 51, 894–898 (2017). https://doi.org/10.3103/S0146411617080168
Received:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411617080168