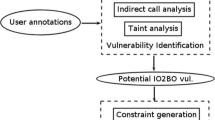
Abstract—
This article proposes an approach to identifying integer overflow vulnerabilities in software represented by the executable code of x86 architecture. The approach is based on symbolic code execution and initially twofold representation of memory cells. A truncated control transfer graph is constructed from the machine code of the program, the paths in which are layer-by-layer checked for the feasibility of the vulnerability conditions. The proposed methods were implemented in practice and experimentally tested on the various code samples.




Similar content being viewed by others
REFERENCES
Pechenkin, A.I. and Lavrova, D.S., Modeling the search for vulnerabilities via the fuzzing method using an automation representation of network protocols, Autom. Control Comput. Sci., 2015, vol. 49, no. 8, pp. 826–833.
Pechenkin, A.I. and Nikolskiy, A.V., Architecture of a scalable system of fuzzing network protocols on a multiprocessor cluster, Autom. Control Comp. Sci., 2015, vol. 49, no. 8, pp. 758–765.
Godefroid, P., Microsoft Research, Fuzzing @ Microsoft—A Research Perspective, ACSC 2017.
Boyer, R.S., Elspas, B., and Levitt, K.N., SELECT—a formal system for testing and debugging programs by symbolic execution, Proceedings of the International Conference on Reliable Software, Los Angeles, 1975, pp. 234–245.
King, J.C., Symbolic execution and program testing, Commun. ACM, 1976, vol. 19, no. 7.
Prateek Saxena, Pongsin Poosankam, Stephen McCamant, and Dawn Song, Loop-extended symbolic execution on binary programs, Proceedings of the ACM/SIGSOFT International Symposium on Software Testing and Analysis (ISSTA), 2009.
Chipounov, V., Georgescu, V., Zamfir, C., and Candea, G., Selective symbolic execution, Proceedings of the 5th Workshop on Hot Topics in System Dependability (HotDep), Lisbon, 2009.
Stephens, N., Grosen, J., Salls, C., Dutcher, A., Wang, R., Corbetta, J., Shoshitaishvili, Y., Kruegel, C., and Vigna, G., Driller: Augmenting fuzzing through selective symbolic execution, Network and Distributed System Security Symposium, 2016.
Sang Kil Cha, Avgerinos, T., Rebert, A., and Brumley, D., Unleashing Mayhem on binary code, 2012 IEEE Symposium on Security and Privacy, 2012.
Author information
Authors and Affiliations
Corresponding authors
About this article
Cite this article
Demidov, R.A., Pechenkin, A.I. & Zegzhda, P.D. An Approach to Vulnerability Searching of Integer Overflows in the Executable Program Code. Aut. Control Comp. Sci. 52, 1022–1028 (2018). https://doi.org/10.3103/S0146411618080102
Received:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411618080102