Abstract
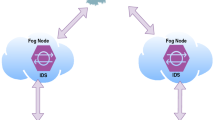
With increase in the demand for Internet of Things (IoT)-based services, the capability to detect anomalies such as malicious control, spying and other threats within IoT-based network has become a major issue. Traditional Intrusion Detection Systems (IDSs) cannot be used in typical IoT-based network due to various constraints in terms of battery life, memory capacity and computational capability. In order to address these issues, various IDSs have been proposed in literature. However, most of the IDSs face problem of high false alarm rate and low accuracy in anomaly detection process. In this paper, we have proposed a anomaly-based intrusion detection system by decentralizing the existing cloud based security architecture to local fog nodes. In order to evaluate the effectiveness of the proposed model various machine learning algorithms such as Random Forest, K-Nearest Neighbor and Decision Tree are used. Performance of our proposed model is tested using actual IoT-based dataset. The evaluation of the underlying approach outperforms in high detection accuracy and low false alarm rate using Random Forest algorithm.


Similar content being viewed by others
REFERENCES
Evans, D., The Internet of Things: How the Next Evolution of the Internet Is Changing Everything, Cisco White Paper, 2011.
Elrawy, M.F., Awad, A.I., and Hamed, H.F.A., Intrusion detection systems for IoT-based smart environments: A survey, J. Cloud Comput., 2018, vol. 7, no. 1, pp. 1–20. https://doi.org/10.1186/s13677-018-0123-6
Etherington, D. and Conger, K., Large DDoS attacks cause outages at Twitter, Spotify, and other sites, TechCrunch, 2016.
Hajiheidari, S., Wakil, K., Badri, M., and Navimipour, N.J., Intrusion detection systems in the Internet of things: A comprehensive investigation, Comput. Networks, 2019, vol. 160, pp. 165–191. https://doi.org/10.1016/j.comnet.2019.05.014
Stojmenovic, I., Fog computing: A cloud to the ground support for smart things and machine-to-machine networks, 2014 Australas. Telecommun. Networks Appl. Conf. ATNAC 2014, 2015, pp. 117–122. https://doi.org/10.1109/ATNAC.2014.7020884
Chaabouni, N., Mosbah, M., Zemmari, A., Sauvignac, C., and Faruki, P., Network intrusion detection for IoT security based on learning techniques, IEEE Commun. Surv. Tutorials, 2019, vol. 21, no. 3, pp. 2671–2701. https://doi.org/10.1109/COMST.2019.2896380
Pahl, M.O. and Aubet, F.X., All eyes on you: Distributed multi-dimensional IoT microservice anomaly detection, 14th Int. Conf. Netw. Serv. Manag. CNSM 2018 Work. 1st Int. Work. High-Precision Networks Oper. Control. HiPNet 2018 1st Work. Segm. Routing Serv. Funct. Chain. SR+SFC 2, 2018, pp. 72–80.
Hasan, M., Islam, M.M., Zarif, M.I.I., and Hashem, M.M.A., Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches, Internet Things, 2019, vol. 7, artic. no. 100059. https://doi.org/10.1016/j.iot.2019.100059
Pajouh, H.H., Javidan, R., Khayami, R., Dehghantanha, A., and Choo, K.K.R., A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks, IEEE Trans. Emerg. Top. Comput., 2019, vol. 7, no. 2, pp. 314–323. https://doi.org/10.1109/TETC.2016.2633228
Kumar, V., Das, A.K., and Sinha, D., UIDS: A unified intrusion detection system for IoT environment, Evol. Intell., 2019, artic. no. 0123456789. https://doi.org/10.1007/s12065-019-00291-w
Deng, L., Li, D., Yao, X., Cox, D., and Wang, H., Mobile network intrusion detection for IoT system based on transfer learning algorithm, Cluster Comput., 2019, vol. 22, pp. 9889–9904. https://doi.org/10.1007/s10586-018-1847-2
Prabavathy, S., Sundarakantham, K., and Shalinie, S.M., Design of cognitive fog computing for intrusion detection in Internet of Things, J. Commun. Networks, 2018, vol. 20, no. 3, pp. 291–298. https://doi.org/10.1109/JCN.2018.000041
Liu, X., Liu, Y., Liu, A., and Yang, L.T., Defending ON-OFF attacks using light probing messages in smart sensors for industrial communication systems, IEEE Trans. Ind. Inf., 2018, vol. 14, no. 9, pp. 3801–3811. https://doi.org/10.1109/TII.2018.2836150
Diro, A. and Chilamkurti, N., Distributed attack detection scheme using deep learning approach for Internet of Things, Future Gener. Comput. Syst., 2018, vol. 82, pp. 761–768. https://doi.org/10.1016/j.future.2017.08.043
Anthi, E., Williams, L., and Burnap, P., Pulse: An adaptive intrusion detection for the internet of things, IET Conf. Publ., 2018, vol. 2018, no. CP740. https://doi.org/10.1049/cp.2018.0035
Benmessahel, I., Xie, K., Chellal, M., and Semong, T., A new evolutionary neural networks based on intrusion detection systems using locust swarm optimization, Evol. Intell., 20190, vol. 12, no. 2, pp. 131–146. https://doi.org/10.1007/s12065-019-00199-5
Mehmood, A., Mukherjee, M., Ahmed, S.H., Song, H., and Malik, K.M., NBC-MAIDS: Naïve Bayesian classification technique in multi-agent system-enriched IDS for securing IoT against DDoS attacks, J. Supercomput., 2018, vol. 74, no. 10, pp. 5156–5170. https://doi.org/10.1007/s11227-018-2413-7
Benesty, J., Chen, J., Huang, Y., and Cohen, I., in Noise Reduction in Speech Processing, Springer, 2009. https://doi.org/10.1007/978-3-642-00296-0
Trent, S.C., Artiles, A.J., and Englert, C.S., From deficit thinking to social constructivism: A review of theory, research, and practice in special education, Rev. Res. Educ., 1998, vol. 23, pp. 277–307. https://doi.org/10.2307/1167293
Reddy, G.T., Kaluri, R., Reddy, P.K., Lakshmanna, K., Koppu, S., and Rajput, D.S., A novel approach for home surveillance system using IoT adaptive security, Proceedings of International Conference on Sustainable Computing in Science, Technology and Management (SUSCOM), Amity University Rajasthan, Jaipur - India, February 26–28, 2019, 2019, pp. 1616–1620. https://doi.org/10.2139/ssrn.3356525
Talia, D., Trunfio, P., and Marozzo, F., Data Analysis in the Cloud: Models, Techniques and Applications, Elsevier, 2015.
da Costa, K.A.P., Papa, J.P., Lisboa, C.O., Munoz, R., and de Albuquerque, V.H.C., Internet of Things: A survey on machine learning-based intrusion detection approaches, Comput. Networks, 2019, vol. 151, pp. 147–157. https://doi.org/10.1016/j.comnet.2019.01.023
DS2OS traffic traces, Kaggle. https://www.kaggle.com/francoisxa/ds2ostraffictraces. Accessed September 25, 2019.
Swarna Priya, R.M., et al., An effective feature engineering for DNN using hybrid PCA-GWO for intrusion detection in IoMT architecture, Comput. Commun., 2020, vol. 160, pp. 139–149. https://doi.org/10.1016/j.comcom.2020.05.048
Milosevic, J., Regazzoni, F., and Malek, M., Malware threats and solutions for trustworthy mobile systems design, Hardware Security and Trust: Design and Deployment of Integrated Circuits in a Threatened Environment, Springer, 2017.
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
The authors declare no conflicts of interest.
About this article
Cite this article
Prabhat Kumar, Gupta, G.P. & Tripathi, R. Design of Anomaly-Based Intrusion Detection System Using Fog Computing for IoT Network. Aut. Control Comp. Sci. 55, 137–147 (2021). https://doi.org/10.3103/S0146411621020085
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411621020085