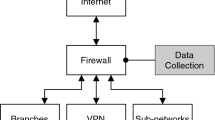
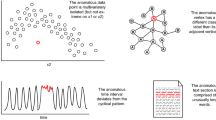
Abstract
A method for solving the problem of localizing the initial cause (root cause) of an anomaly in a distributed information computer system has been described. The main idea of the proposed approach consists in an approximate estimation of the set of elements of a distributed information computer system containing the source of the anomaly. Two algorithms have been used to describe the root cause of the anomaly: an algorithm that generates a parameter that indicates the anomaly, and a mapping algorithm. There is fragmentary information about the first algorithm and reliable information that there is an anomalous transformation in it. The second algorithm is simple and allows detecting the anomaly. The anomaly is detected by the abnormal parameter values that these algorithms calculate. Such parameters are called integral parameters. A number of properties of integral parameters and connections of these algorithms have been investigated. Methods for searching the region of the root cause of the anomaly using chains of integral parameters have been developed.
Similar content being viewed by others
REFERENCES
Steenwinckel, B., Adaptive anomaly detection and root cause analysis by fusing semantics and machine learning, The Semantic Web: ESWC 2018 Satellite Events, Gangemi, A., Gentile, A.L., Nuzzolese, A.G., Rudolph, S., Maleshkova, M., Paulheim, H., Pan, J.Z., and Alam, M., Eds., Lecture Notes in Computer Science, vol. 11155, Cham: Springer, 2018, pp. 272–282. https://doi.org/10.1007/978-3-319-98192-5_46
Grusho, A., Grusho, N., and Timonina, E., The bans in finite probability spaces and the problem of small samples, Distributed Computer and Communication Networks. DCCN 2019, Vishnevskiy, V., Samouylov, K., and Kozyrev, D., Eds., Lecture Notes in Computer Science, vol. 11965, Cham: Springer, 2019, pp. 578–590. https://doi.org/10.1007/978-3-030-36614-8_44
Grusho, A.A., Zabezhailo, M.I., Grusho, N.A., and Timonina, E.E., Concepts forming on the basis of small samples, Inf. Ee Primen., 2019, vol. 13, no. 4, pp. 81–84. https://doi.org/10.14357/19922264190413
Grusho, A., Grusho, N., and Timonina, E., Method of several information spaces for identification of anomalies, Intelligent Distributed Computing XIII. IDC 2019, Kotenko, I., Badica, C., Desnitsky, V., El Baz, D., and Ivanovic, M., Eds., Studies in Computational Intelligence, vol. 868, Cham: Springer, 2020, pp. 515–520. https://doi.org/10.1007/978-3-030-32258-8_60
Lim, S., Kalinin, M., and Zegzhda, P., Bioinspired intrusion detection in ITC infrastructures, in Technological Transformation: A New Role for Human, Machines and Management. TT 2020, Schaumburg, H., Korablev, V., and Ungvari, L., Eds., Cham: Springer, 2021, pp. 10–22. https://doi.org/10.1007/978-3-030-64430-7_2
Lavrova, D., Poltavtseva, M., and Shtyrkina, A., Security analysis of cyber-physical systems network infrastructure, IEEE Industrial Cyber-Physical Systems (ICPS), St. Petersburg, 2018, IEEE, 2018, pp. 818–823. https://doi.org/10.1109/ICPHYS.2018.8390812
Zegzhda, P., Zegzhda, D., Kalinin, M., Pechenkin, A., Minin, A., and Lavrova, D., Safe integration of SIEM systems with Internet of Things: Data aggregation, integrity control, and bioinspired safe routing, Proc. 9th Int. Conf. on Security of Information and Networks, Newark, N.J., 2016, New York: Association for Computing Machinery, 2016, pp. 81–87. https://doi.org/10.1145/2947626.2947639
Jurn, J.S., Kim, T., and Kim, H., A survey of automated root cause analysis of software vulnerability, Innovative Mobile and Internet Services in Ubiquitous Computing. IMIS 2018, Barolli, L., Xhafa, F., Javaid, N., and Enokido, T., Eds., Cham: Springer, 2019, pp. 756–761. https://doi.org/10.1007/978-3-319-93554-6_74
Brandon, A., Solé, M., Huélamo, A., Solans, D., Pérez, M.S., and Muntés-Mulero, V., Graph-based root cause analysis for service-oriented and microservice architectures, J. Syst. Software, 2020, vol. 159, p. 110432. https://doi.org/10.1016/j.jss.2019.110432
Nikolaeva, E.K., “Sem’ instrumentov kachestva” v yaponskoi ekonomike (Seven Quality Tools in Japan Economy), Moscow: Izd. Standartov, 1990.
Latino, M.A., Latino, R.J., and Latino, K., Root Cause Analysis: Improving Performance for Bottom-Line Results, CRC Press, 2016, 4th ed.
Sutton, M., Greene, A., and Amini, P., Fuzzing: Brute Force Vulnerability Discovery, Pearson Education, 2007.
Zegzhda, P.D., Poltavtseva, M.A., Pechenkin, A.I., Lavrova, D.S., and Zaitseva, E.A., A use case analysis of heterogeneous semistructured objects in information security problems, Autom. Control Comput. Sci., 2018, vol. 52, no. 8, pp. 918–930. https://doi.org/10.3103/S0146411618080278
Grusho, A.A., Zabezhailo, M.I., Smirnov, D.V., and Timonina, E.E., On probabilistic estimates of the validity of empirical conclusions, Inf. Ee Primen., 2020, vol. 14, no. 4, pp. 3–8. https://doi.org/10.14357/19922264200401
Zegzhda, D., Lavrova, D., and Poltavtseva, M., Multifractal security analysis of cyberphysical systems, Nonlin. Phenom. Complex Syst. (Minsk, Belarus), 2019, vol. 22, no. 2, pp. 196–204.
Dakhnovich, A.D., Moskvin, D.A., and Zegzhda, D.P., Analysis of the information security threats in the digital production networks, Autom. Control Comput. Sci., 2018, vol. 52, no. 8, pp. 1071–1075. https://doi.org/10.3103/S0146411618080369
Zegzhda, D., Lavrova, D., and Khushkeev, A., Detection of information security breaches in distributed control systems based on values prediction of multidimensional time series, IEEE Int. Conf. on Industrial Cyber Physical Systems (ICPS), Taipei, 2019, IEEE, 2019, pp. 780–784. https://doi.org/10.1109/ICPHYS.2019.8780304
Lavrova, D., Zaitceva, E., and Zegzhda, P., Bio-inspired approach to self-regulation for industrial dynamic network infrastructure, CEUR Workshop Proc., Moscow, 2019, Basarab, M. and Markov, A.S., Eds., Moscow: CEUR Workshop Proceedings, 2019, pp. 34–39.
Funding
The study was partially supported by the Russian Foundation for Basic Research, project no. 18-29-3081.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
The authors declare that they have no conflicts of interest.
Additional information
Translated by S. Avodkova
About this article
Cite this article
Grusho, A.A., Grusho, N.A., Zabezhailo, M.I. et al. Localization of the Root Cause of the Anomaly. Aut. Control Comp. Sci. 55, 978–983 (2021). https://doi.org/10.3103/S0146411621080137
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.3103/S0146411621080137